NW Scheduler (New World Scheduler) is a software program for Jehovah’s Witnesses to help with scheduling and organizing your congregation. Easy. Simple. Fast.
About NW SCHEDULER
New World Scheduler is available in over 100 languages
It is used by thousands of congregations and tens of thousands of elders in 174 countries
It can be installed on Windows and on Apple Mac computers
Data is stored on your local computer only and implements modern security best-practises
The companion NW Publisher app is used by over 1 million publishers
NEW WORLD SCHEDULER Features
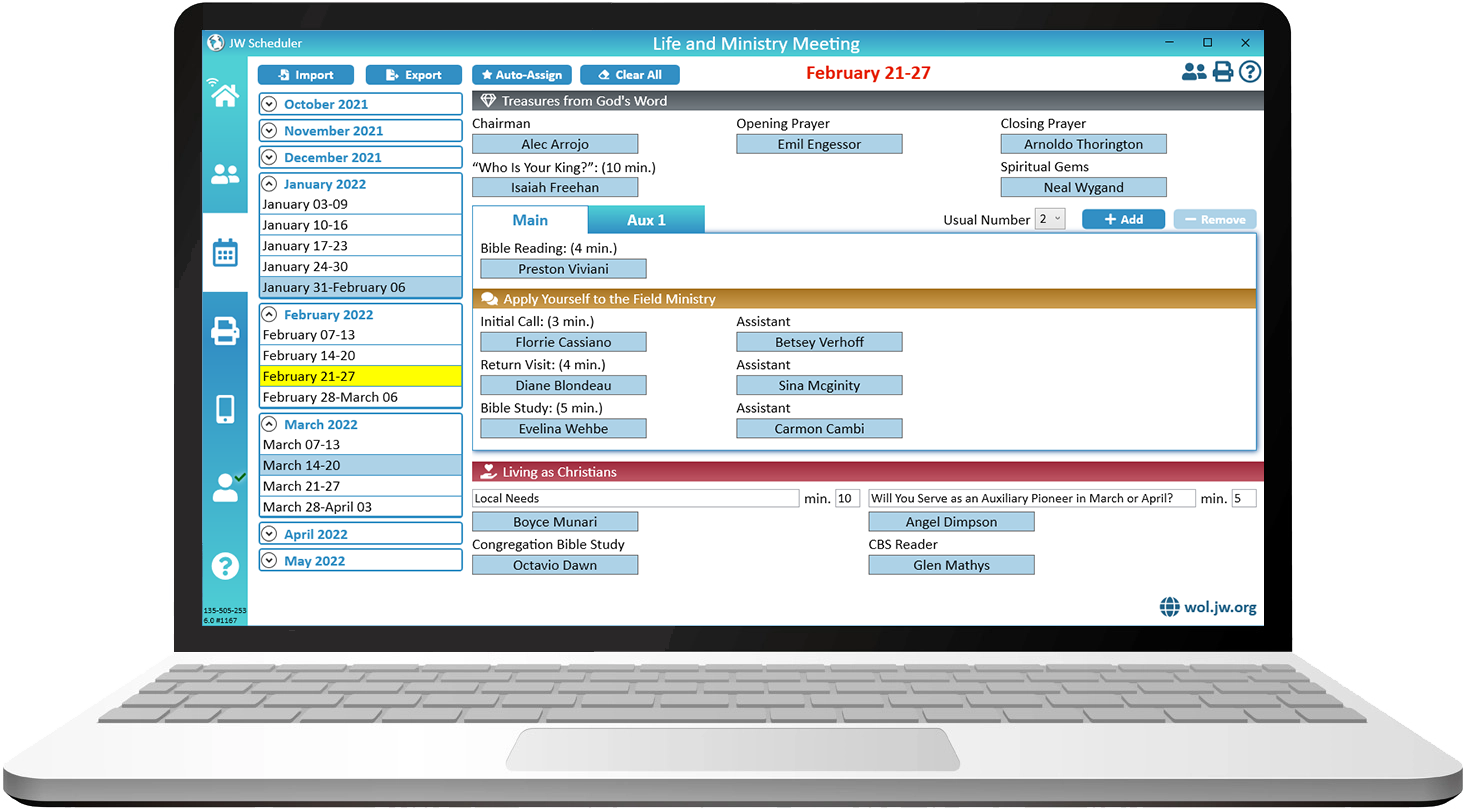
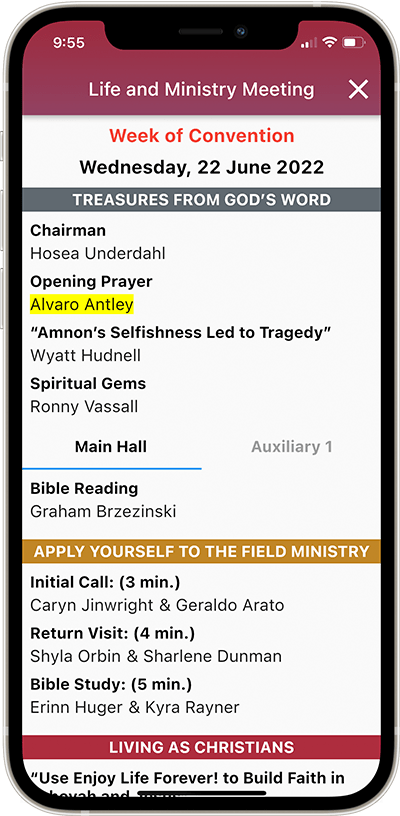
New World Scheduler can quickly and easily schedule all parts of Christian Life and Ministry (CLM) meeting, including Main & Auxiliary classes. Supports Auto-Assign, recommended student and detailed Part History.
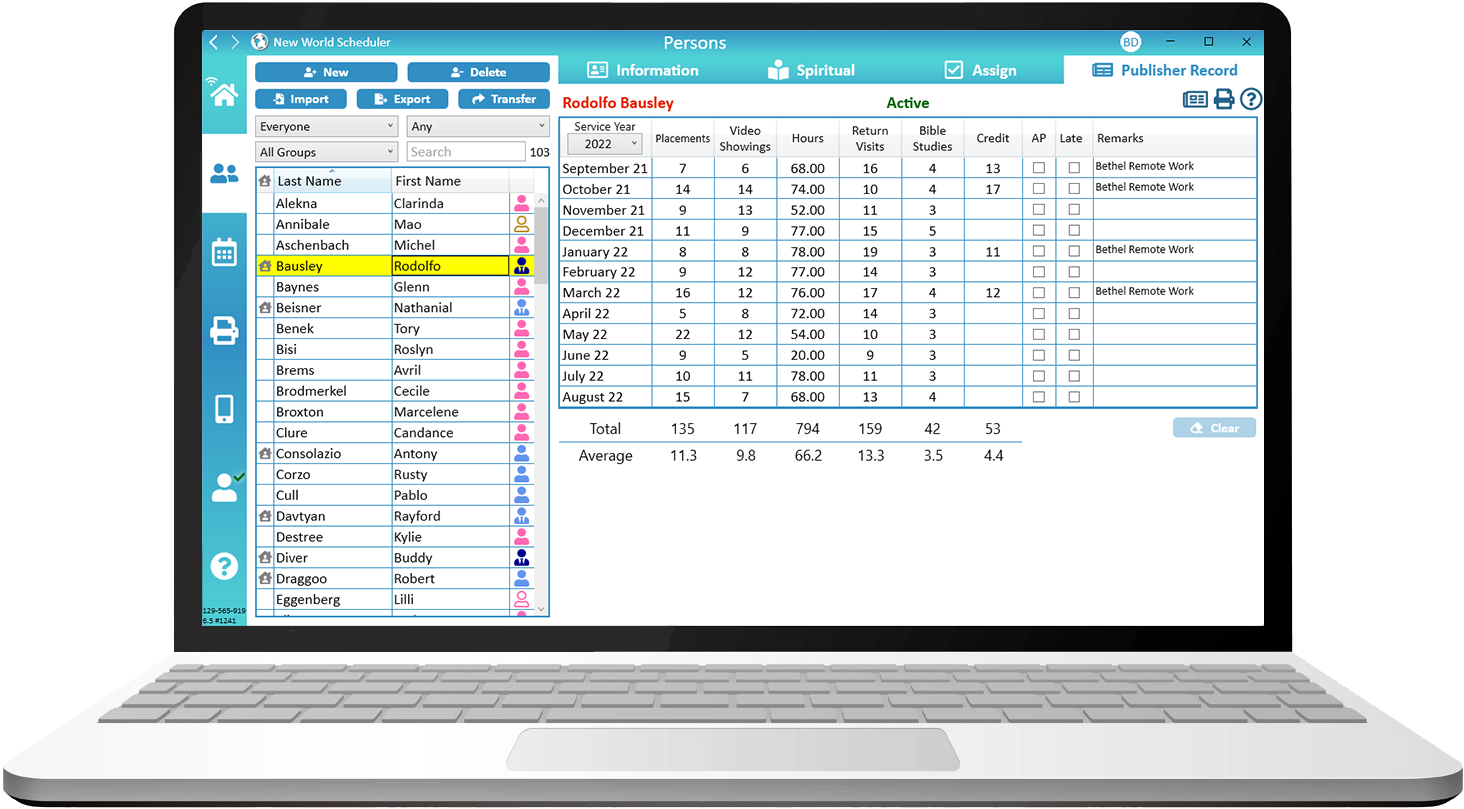
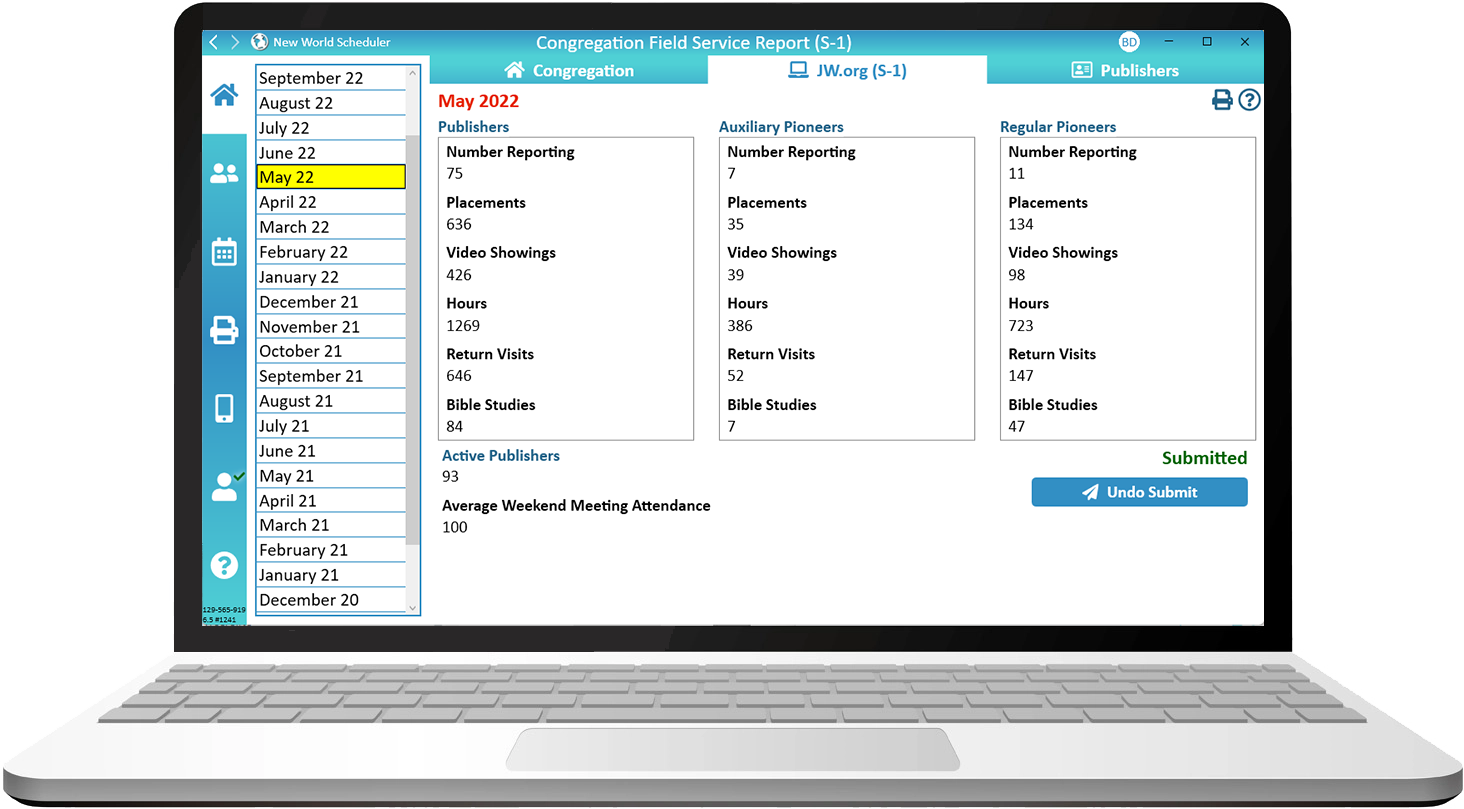
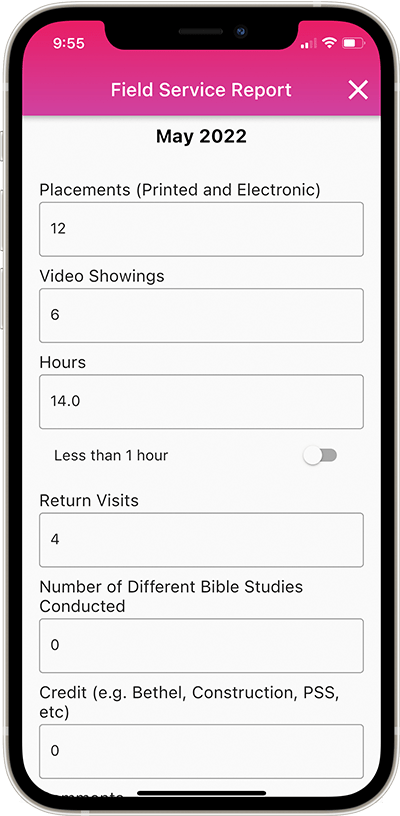
Congregation Secretaries can use NW Scheduler to enter Field Service Reports, maintain Congregation Publisher Records, compile the Monthly Congregation Field Service Report, print S-21 Publisher Record Cards and more.
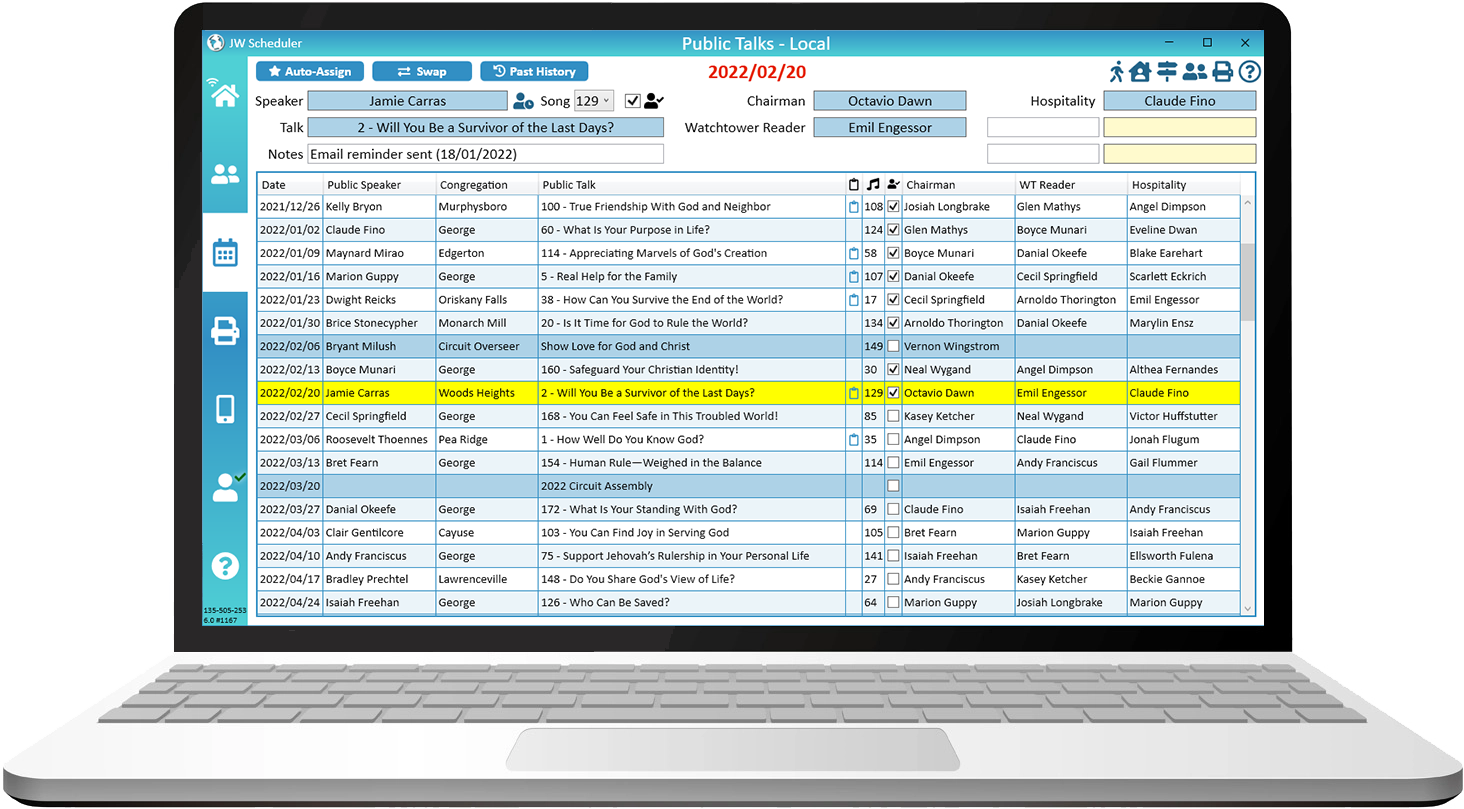
The Public Talk Coordinator can schedule Local and Away Public Talks, including visiting speakers and hospitality. Neighbor Congregations and Public Speakers can be entered, along with meeting times and locations.
New World Scheduler can create and manage congregation Territories and maps, including Territory Boundaries, Territory Information, Territory Addresses, Territory Assignments and Territory Maps.
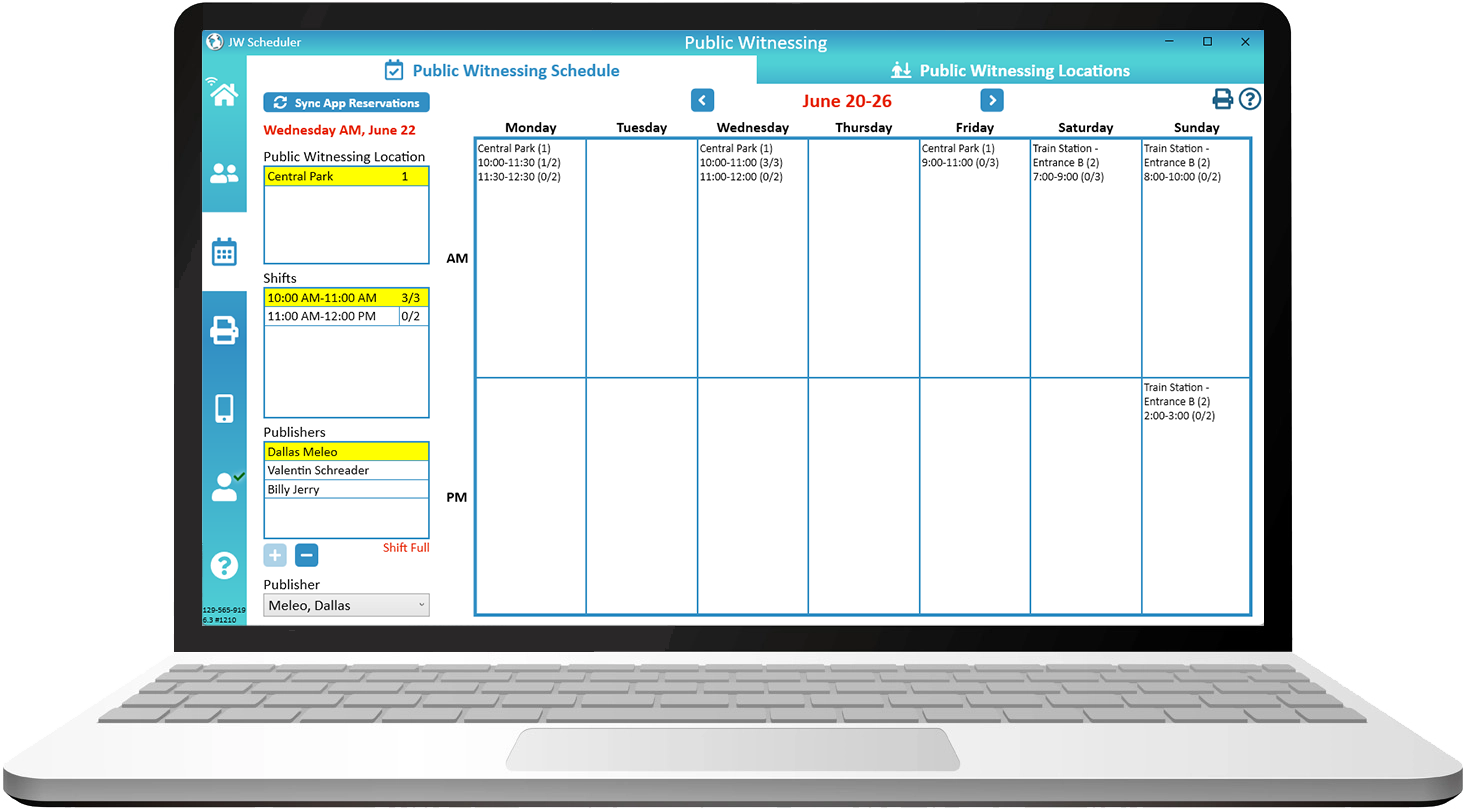
Field Service schedules can be scheduled by the Service Overseer, including Early Morning and Evening witnessing. The Conductor, Location and map can be entered, as well as any specific Group Field Service arrangements.
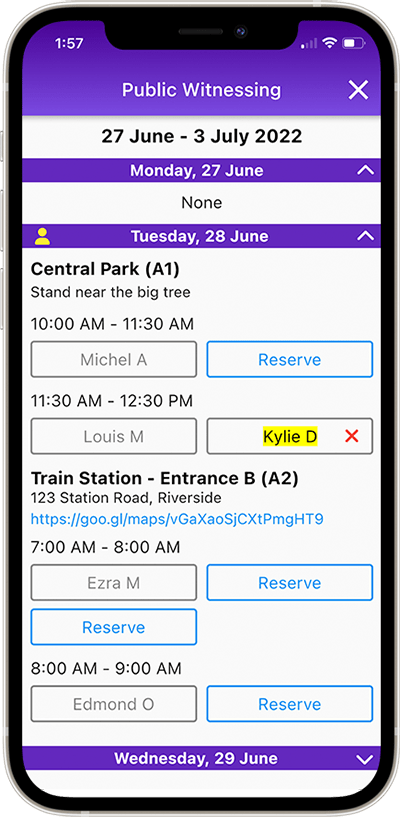
Public Witnessing carts, locations and shifts can be setup in New World Scheduler, and approved publishers can use NW Publisher app to reserve any Public Witnessing shift.
Maintenance Tasks can be scheduled per month, or several months, and can be assigned to publishers, groups or shared with congregations sharing your Kingdom Hall.
Congregation Duties can be scheduled, including Attendants, Security, Sound, Video, Microphones, Platform and even Custom duties. Can be scheduled Per Week or Per Meeting.
Circuit Overseer Visits can scheduled, including all Meetings, Field Service, Shepherding Visits and Meal Arrangements. All information required by the CO can be quickly and easily generated in NW Scheduler.
Kingdom Hall Cleaning can be scheduled in New World Scheduler, including Weekly Hall Cleaning and After Meeting Clean. One or more groups can be assigned.
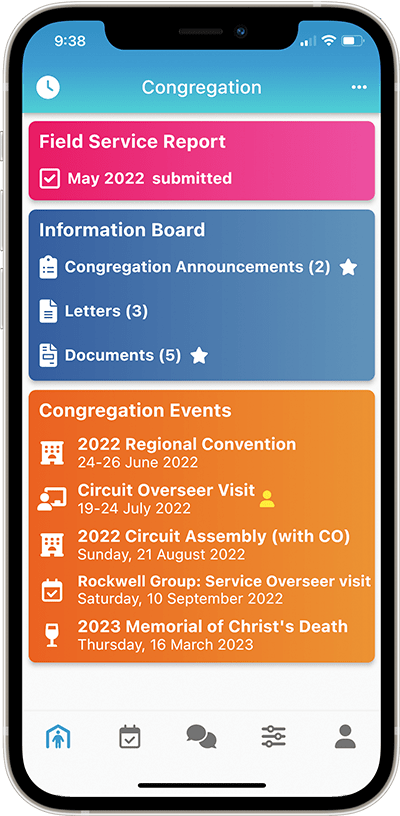
The Congregation Information Board acts as a “virtual Information Board” and contains Congregation Announcements, Documents and Letters.
NW Scheduler can quickly and easily manage and receive Literature Requests from publishers.
Securely store and manage Publishers Contact Information and Emergency Contacts.
Tasks allow you to keep track of any congregation tasks you must perform, as well as assign and track tasks for others.
NW SCHEDULER Special Features
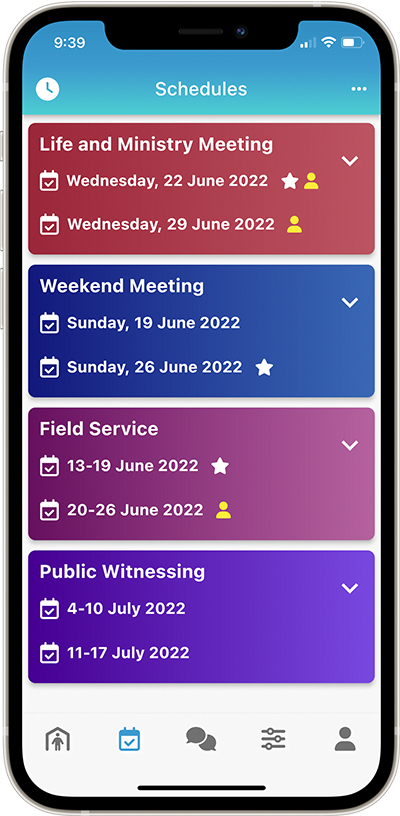
Publishers can see upcoming Christian Life and Ministry meeting assignments and schedules, Public Talk assignments and schedules, Field Service assignments and schedules, Duties and Cleaning assignments and more.
Publishers can also submit their Field Service Report, send Away Periods, make Literature Requests, and view Territories assigned to them, and more!
Congregation Sharing helps all elders keep full up-to-date with what is happening in the Congregation.
Data is accurate and secure. Errors are reduced. Training new brothers is easier. Everyone saves time.
Share your Public Speakers automatically with other congregations in your Circuit. Request and Approve Public Speaker exchanges automatically via NW Scheduler.
Who can use NW Scheduler?
Schedule all non-student parts of the midweek Life and Ministry Meeting and maintain Congregation Assignments.
Enter Field Service Reports, maintain Publisher Record cards and submit the monthly Field Service report.
Schedule all student parts of the midweek Christian Life and Ministry Meeting (CLM), print reports and assignment slips.
Schedule congregation Field Service meetings, create and maintain congregation Field Service Groups.
See the field service information of all members in their group, so they can promptly follow-up and provide assistance.
Organize Congregation Maps and Territories, including checking out to publishers and printing S-13 Records.
Schedule Local and Away Public Talks, add and maintain Public Speakers, including both local and neighbour congregations.
Who else can use NW Scheduler?
Create and assign Custom Tasks to publishers to complete certain Maintenance Tasks.
Manage and organize Literature Items and Literature Requests from publishers.
Schedule congregation Kingdom Hall cleaning and Lawn and Garden care.
Schedule congregation duties such as Attendants, Security, Car Park, as well as record the Meeting Attendance.
Schedule congregation duties such as Sound, Video, Microphones, Platform and Zoom Host.
See all the above data and keep up-to-date with everything that is happening in the congregation.
Can securely receive your congregation data and check all aspects of your congregation before his visit.
NW SCHEDULER Advantages
New World Scheduler can organise & schedule practically everything. Maintain just one list of publishers shared with all appointed brothers, which saves time, reduces mistakes and makes training quicker and easier.
NW Scheduler takes data security and privacy very seriously, implementing modern security best-practises. By default, data is stored on your local computer only and is encrypted.
NW Scheduler has been designed to be simple and very easy for anyone to use. Learn to use New World Scheduler in just a few minutes, and make schedules quickly and easily. Save time for more important things.
New World Scheduler produces attractive, practical and appealing Christian Life and Ministry meeting, Public Talk, Duties and Kingdom Hall Cleaning reports. Reports can be saved in Document or PDF format.
Save time by using Auto-Assign to generate the first draft of your new schedules. This will automatically select the most appropriate member for a part, and ensure no conflicts occur. You can then make any adjustments.
New World Scheduler seamlessly exports data to Timothy and Circuit Assistant, which are software programs used by many Circuit Overseers. This saves them time and helps them organize the congregations in their circuit.
New World Scheduler is now available in over 100 languages and is one of the most widely translated programs in the world! New languages are regularly added, and you can Request a New Language for New World Scheduler.
NW Scheduler includes very powerful Email Special Features . E.G. the LMMO can send Assignment Slips to each student who has a part. The Secretary can send a Field Service Summary to each Group Overseer, and much much more.
NW Scheduler Reviews and Testimonials
NW Scheduler is used by thousands of congregations, tens of thousands of appointed brothers in 174 countries, and our NW Publisher app is used by over 1 million publishers! We receive lots of encouraging comments and feedback every day, and are happy to share some of these.
To see all reviews and testimonials, including what brothers in your area think of New World Scheduler, see All Reviews and Testimonials.
Very well thought out, intuitive, and easy to use
Thorough and comprehensive program and database to track all scheduling needs for the Congregation. Very well thought out, intuitive, and easy to use. There is exhaustive Help information to answer any questions that arise. The program just works splendidly and I recommend it to any Congregation! Very nice work brothers and sisters – thank you! Jehovah is certainly blessing your work.
August 2023
I literally cannot believe what a massive organizational upgrade we were given in a short period of time using this platform
The scriptures that come to mind is that:
1) God not a God of disorder and
2) let all things take place … by arrangment
This app has been indispensable as regards reporting of field service time, arranging the cart preaching at different locations, knowing every single assigned brother for every duty at the meeting. Before I was scrambling through papers never finding the right schedule and form and now it is all here. I appreciate the reminders such as when to assign an audit.
We are excited to start using the territory feature as we saw a need to have some digital territory delivery during COVID but doing this by email and scanning each territory was time consuming with poor picture quality.
Another great feature is how various brothers with different assignments can all have limited editing roles for attendants, sound and video, talks and so forth.
We looked into the security features of this app versus other ones and we felt comfortable with how NWS does end to end encryption and doesn’t store unencrypted and sensitive data on a public server.
I literally cannot believe what a massive organizational upgrade we were given in a short period of time using this platform. We had reservations about older ones using it, but they love it. It is intuitive and easy to use and they feel a lot more ‘in the know’ about what is going on in the congregation with it.
Thank you!
August 2023
leaps and bounds above others
The application is leaps and bounds above others we have used. The integration is seamless and everything is at your fingertips. We highly recommend your product.
August 2023
very powerful and well thought out
I love the application. It’s very powerful and well thought out. Specifically I really like the reminders of the home page of the task that are needed to be completed and how everyone is connected to keep everyone of the same page. Thank you for your hard work in endeavoring to make our responsibilities easier and more efficient in caring for the congregation.
August 2023
recommended to us by our Circuit Overseer
This application was recommended to us by our Circuit Overseer. It has been a blessing! It is so much easier to track field service reports, keep all responsible brothers up to date, and stay as organized as possible.
July 2023
for every one of us that expresses appreciation to you directly, there are hundreds more that does so in their heart!
I extend my full appreciation for the work that you brothers and sisters have done for us! New World Scheduler has been such a blessing to not just myself in my endeavor to serve Jehovah with my responsibilities, it has also been a blessing to the entire Congregation. Please keep up the good work we have come to depend on it (-;
Thank you for all you do friends. May you always remember that for every one of us that expresses appreciation to you directly, there are hundreds more that does so in their heart!
July 2023
Compare SOFTWARE & APPS
How does New World Scheduler compare with similar programs and apps?
Our intention is not to criticize other software programs, since we are all “standing firm in one spirit, with one soul, striving side by side for the faith of the good news” – Philippians 1:27.
Instead, we invite you to explore the differences between New World Scheduler and these other programs for yourself.
“Thank you for having a ‘Comparison’ page. It was very helpful when trying out new programs!” – Brother Mike, USA
Data can be imported from Majestic KHS, Hourglass app, TSWin, Deckhand, CLM Explorer, Territory Helper, Alba, and CSV file into New World Scheduler.
New World Scheduler strongly believes your congregation and member data is your own, and you should be able to Import and Export your data as you wish. We also believe it is fair and right to allow data exchange between other scheduling programs.
